select the best answer. which of the following are breach prevention best practices
WHO intensifies response to looming health crisis in the greater Horn of Africa as food insecurity worsens June 30 2022. All of the above.

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
Access only the minimum amount of PHIpersonally identifiable information PII necessary.

. Developing policies and procedures and implementing best practices will at the very least diminish the potential. Identify devices that store transmit collect or process sensitive data. Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System.
Best practices for breach prevent are. Are breach prevention best practice. So you have to create solid and high-end passwords for your data.
Those who use SharePoint best practices often follow Microsoft ones too because of their safety and security. Which of the following are breach prevention best practices All of the above. Which of the following are breach prevention best practices Saturday June 11 2022 Edit.
All of this above. The following are high-level best practices for preventing breaches. Promptly retrieve documents containing PHIPHI from.
D All of the above. Conduct a risk assessment before any solution is implemented it is important to know your networks 13. Furthermore many countries have data breach notification laws requiring both private and public entities to notify individuals of breaches involving personal information.
Perform regular vulnerability assessments. True Select the best answer. 30 Best Practices for Preventing a Data Breach.
Identify users with access to sensitive data. When must a HIPAA. C Promptly retrieve documents containing PHIPHI from the printer.
Logoff or lock your workstation when it is unattended. All of this above. Silahkan kunjungi postingan which of the.
Physical measures including policies and procedures that are used to protect electronic information systems and related buildings and equipment from natural and environmental hazards and unauthorized intrusion. B Logoff or lock your workstation when it is unattended. The best way to avoid being a victim of a breach is to prioritize data security.
The typical steps most cybercriminals follow during breach operations are. A Systems of Records Notice SORN serves as a notice to the public about a system of records and must. Promptly retrieve documents containing PHIPHI from the printer.
The following best practices may help. Identify areas that store transmit collect or process sensitive data. Vulnerability assessment is the process intended to identify classify and prioritize security threats and determine the risks.
Access only the minimum amount of PHIpersonally identifiable information PII necessary B. Those who use SharePoint best practices often follow Microsoft ones too because of their safety and security. Logoff or lock your workstation when it is unattended.
Which of the following are breach prevention best practices. Vulnerability assessment is the process intended to identify classify and prioritize security threats and determine the risks. Furthermore many countries have data breach notification laws requiring both private and public entities to notify individuals of breaches involving personal information.
Select the best answer. World Bank Board Approves New Fund for Pandemic Prevention Preparedness and Response PPR June 30 2022. Want to read the entire page.
Select the best answer. A Access only the minimum amount of PHIpersonally identifiable information PII necessary. Best practices for breach prevent are.
Course Hero member to access this document. Select the best answer. Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022.
Upload your study docs or become a. Access only the minimum amount of PHIpersonally. Check spelling or type a new query.
Developing the IRP will help the IT staff of the company to control the data breach incidents. Question and answer. Identity sensitive data collected stored transmitted or processes.
There are Microsoft best practices best practices and practices. Asked Jul 9 in Other by Kamal 334k points Which of the following are breach prevention best practices. 10 best practices for data breach prevention 1.
Which of the following is are breach prevention best practice. Invest in security automation. Select the best answer.
There are Microsoft best practices best practices and practices. Making weak passwords can be a reason for Data Breaches. Which of the following are common causes of breaches.
The e-Government Act promotes the use of electronic government services by the public and improves the use of information technology in the government. After the Development Checks of the Security Program. Companies that leveraged artificial intelligence machine learning analytics and automated.
Create Strong Policies Strong Passwords. New political declaration to halve road traffic deaths and injuries by 2030 is a milestone achievement June 30 2022. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer.

Protecting Data At Rest Vs Data In Motion Endpoint Protector

Keeping Personal Data Protected From Data Breaches Privacy Policies

Data Loss Prevention Best Practices Endpoint Protector
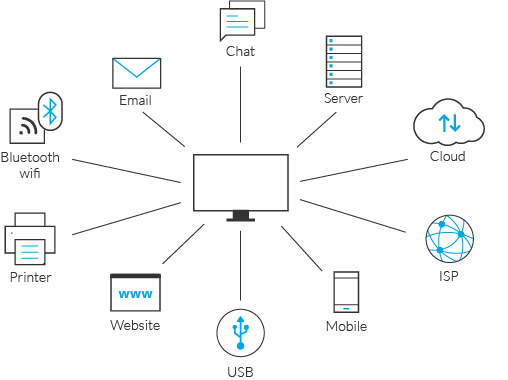
What Is Data Loss Prevention Dlp Data Leakage Mitigation Imperva

Equifax Aftermath How To Protect Against Identity Theft Identity Theft Protection Identity Theft Identity Fraud

Top 12 Data Security Solutions To Protect Your Sensitive Information

Operations Technology Security How To Safeguard Your Assets

All You Need To Know About Hipaa Compliance Endpoint Protector
Frequently Asked Questions About Data Loss Prevention Endpoint Protector

5 Key Principles For Data Security
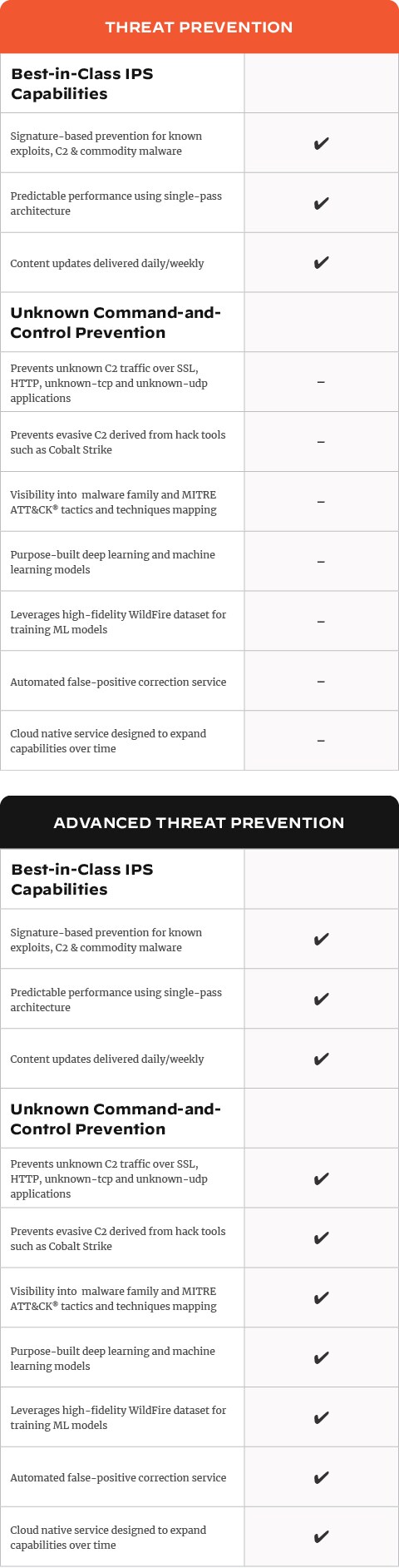
Threat Prevention Palo Alto Networks

How To Prevent Data Breaches 12 Best Practices Paysimple

How To Protect Your Data At Rest Endpoint Protector

Types Of Security Breaches Physical And Digital Maryville Online

Privilege Escalation Attacks Types Examples And Prevention Purplesec
Threat Prevention Palo Alto Networks

The Ultimate Data Breach Response Plan Securityscorecard

6 Best Practices For Protecting Client Confidentiality Titanfile
